Tel Aviv, ISRAEL, December 2nd, 2024, CyberNewsWire
Sweet Security Introduces Evolutionary Leap in Cloud Detection and Response, Releasing First Unified Detection & Response Platform
With Sweet, customers can now unify detection and response for applications, workloads, and cloud infrastructure
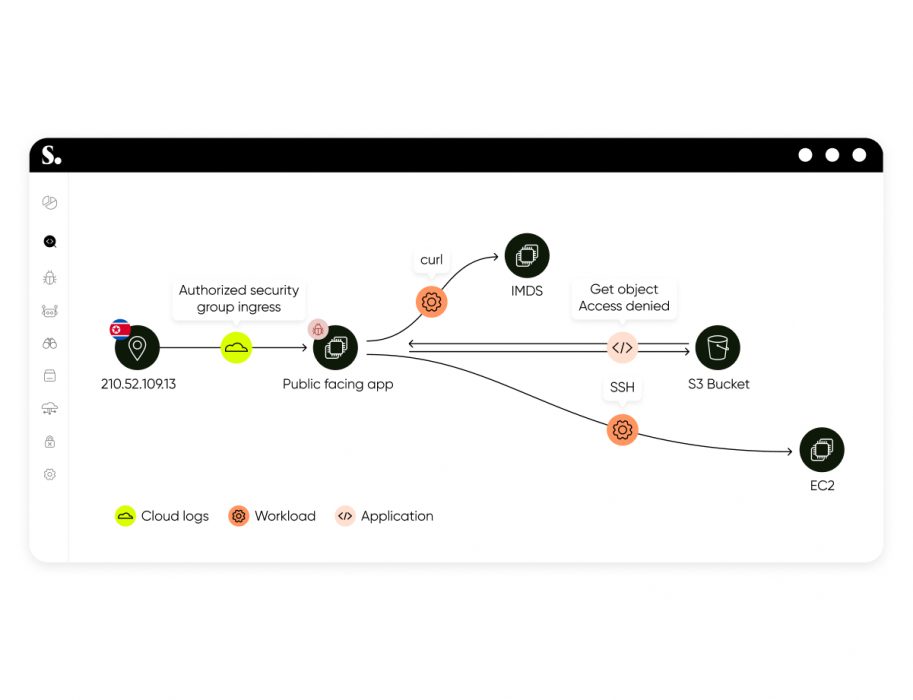
Sweet Security today announced the release of its unified Cloud Native Detection and Response platform, designed to transform the way organizations protect their cloud environments in real time. Sweet’s platform integrates the capabilities of Application Detection and Response (ADR), Cloud Detection and Response (CDR), and Cloud Workload Protection Platform (CWPP) into one comprehensive solution. This innovative approach delivers unparalleled detection and response capabilities, unifying insights from every layer of the cloud stack.
“The Sweet team has worked tirelessly to build a platform that not only meets the needs of today’s security landscape but also anticipates the challenges of tomorrow,” said Dror Kashti, CEO of Sweet. “With our supercharged detection and response capabilities, we’re providing organizations with the tools they need to secure their cloud environments faster and more effectively than ever before.”
In an era where security teams face an average dwell time of 10 days to resolve cloud incidents due to lack of context, Sweet Security empowers organizations to put detection and response at the forefront of their cloud defense strategy, providing the ability to act on threats as they happen and ensuring an incident never becomes a breach. When detection and response is siloed between application, workload, and cloud infrastructure levels, it results in fragmented alerts that require security teams to piece together in order to understand the scope of the attack.
“Sweet Security’s Cloud Native Detection and Response platform has been a game changer for us,” said Shai Sivan, CISO at Kaltura. “The ability to unify visibility across both application activity and infrastructure changes has been crucial in gathering the forensic data we need. With average detection times of just 30 seconds and the ability to respond to incidents in 2-5 minutes, Sweet has decreased our Mean Time to Resolution (MTTR) by an impressive 90%, allowing us to respond faster and more effectively.”
In addition to unified detection and response, Sweet Security’s platform is equipped with a suite of next-generation capabilities that are powered by GenAI, including:
- Unified Cloud Visibility
- Vulnerability Management
- Runtime CSPM
- Identity Threat Detection & Response (ITDR)
James Berthoty, cloud expert and owner of Latio Tech, recently commented on Sweet Security’s unified solution, stating, “Cloud Application Detection & Response is all about combining cloud, workload, and application layer contexts into a single storyline to make incident response in the cloud finally a reality. For too long we’ve been content with mediocre visibility into our most important assets. Sweet is on the frontlines of changing that by giving teams the cross-layer visibility they’ve needed for years.”
Book a meeting with Sweet Security at AWS re:Invent 2024 in Las Vegas here.
About Sweet Security
Specializing in Cloud Native Detection & Response (D&R), Sweet Security protects cloud environments in real time. Founded by the IDF’s former CISO, Sweet’s solution unifies threats insights from cloud applications, workloads and infrastructure. Leveraging a lean, eBPF-based sensor and deep behavioral analysis, Sweet analyzes anomalies, generating vital insights on incidents, vulnerabilities, and non-human identities. Its GenAI-infused technology cuts through the noise and delivers actionable recommendations on critical, real-time cloud risks. Privately funded, Sweet is backed by Evolution Equity Partners, Munich Re Ventures, Glilot Capital Partners, CyberArk Ventures and an elite group of angel investors.
For more information, please visit http://sweet.security.